Developing a website?
If you are a web developer or a web designer, you must be informed of the three key elements needed to develop a website.
For designing a website blow are the three key elements:
- Hypertext Markup Language – HTML
- Cascading Style Sheets – CSS
- JavaScript – JS.
HTML controls all the structure of the document. The flow of data on your website.
CSS describes the display of the arrangement, how your website looks?
And, JS handles all the interactions. The interactions between your customers and the website.
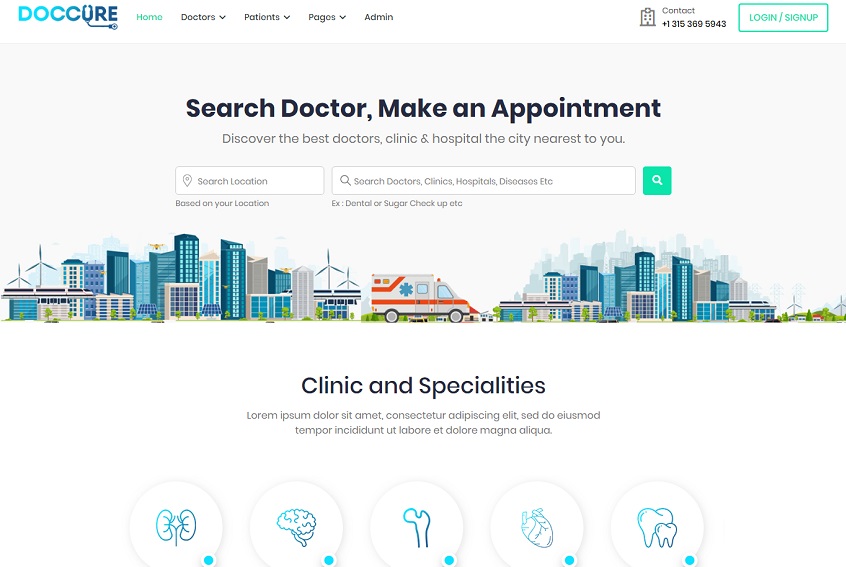
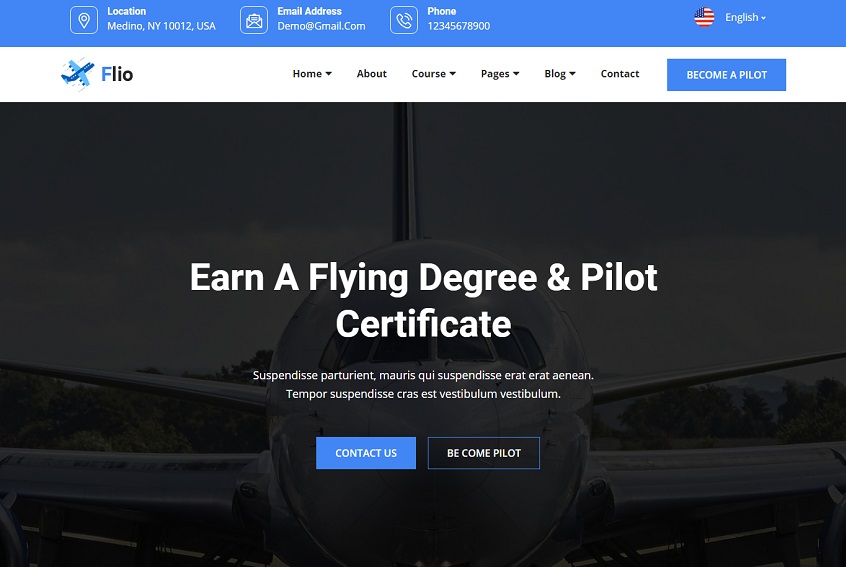
A website contains several web pages. You must design and develop every web page as interesting and attractive as possible. And, if you are looking for the most perfect design, your search will end here.
PHP is considered the best language for developing dynamic web pages. You can easily download FREE PHP projects on different topics according to your requirements.
At Templates Hub, we have HTML website templates with a predefined collection of required web pages designed especially for different professionals and businesses.
We have a collection of more than 400 free website templates and WordPress themes using which you can build an eCommerce websites to sell your products online or a landing page for marketing or a business portfolio.
Our templates are ready to publish, and you can even customize them according to your needs. Now, your dream website can be achievable in just a few minutes with Templates Hub.
How to choose a website template?
TemplatesHub templates are developed with responsive web design techniques, so they look awesome across all devices.
A mobile-friendly website is necessary for your business because the number of mobile users increasing rapidly. There are some major factors to be considered while deciding a website template for mobile, Clickable areas and Buttons should be touch-friendly for the best user experience.
- To operate easily the size of buttons must be comparable to the ideal fingertip size.
- The website should be beautiful and attractive. This ensures the number of returning visitors.
- To keep the website bounce rate low the user interface must be easy.
We have designed the best of the best free website templates just for you by considering all these factors.
How much does website templates cost TemplatesHub?All our website templates are free.
..
Free Download Premium Game Trainers and cheats. Geeks Blue/
Best monitors with built in speakers Monitor Finder